Hacking democracies
Cataloguing cyber-enabled attacks on elections
Foreword
One of the great hopes for the internet was that it would herald a new era in the democratisation of information. To a large extent, it’s been successful. So successful, in fact, that global platforms, technology diffusion and mobility have brought some unintended consequences by enabling the rapid dissemination of disinformation and fake news.
We live in a time when trust in our democratic and other key institutions has declined, and this is compounded by new capabilities of adversaries seeking to interfere in our elections and to undermine people’s trust in those institutions.
In this policy brief, the writers explore areas where interference has been detected across the world and consider key learnings from those examples in order to develop policy responses for countering each type of interference.
Technology has the power to transform lives by reducing barriers to entry and creating greater equity so that all our citizens can participate in education and the economy. We want to live in a world where friction is removed and technology enhances our experience, where all citizens have access to the internet, and where we can vote electronically in elections. However, our interconnection needs to be safe and trusted, protecting and enhancing our democracies.
This brief starts an important national conversation, generating awareness of the approaches commonly taken by adversaries to spread disinformation, misinformation and fake news. It lays out a series of measures for managing risk, and serves as an educational resource for our citizens on what to keep an eye out for, and how to better distinguish reputable information from disinformation in real time.
Yohan Ramasundara
President, Australian Computer Society
What’s the problem?
Analysis of publicly known examples of cyber-enabled foreign interference in elections reveals key challenges. First, while perceptions of interference are widespread, the actors are few—Russia and China—and the effort is highly targeted. Russia is targeting the US and Europe (with a few forays into South America), while China targets its region (having, for the moment, reached as far as Australia).
Second, the methods used can be hard to pick up and democracies seem poorly equipped to detect intrusions, being traditionally focused on external intelligence collection. Adversaries are able to enter public debates, infiltrate legitimate activist networks and even enter the mainstream media as trusted commentators. Significant activity may be being missed. Finally, while opinion polling shows concerning levels of dissatisfaction with democracy and weakening trust in public institutions, it’s very difficult to assess the impact of election interference on those phenomena. It’s likely to have some impact but be outweighed by larger societal factors.
What’s the solution?
First, the response from democracies should be calibrated to the likely risk and adversary. The US and European states are clear targets of Russia; Indo-Pacific nations are targets of the Chinese Communist Party (CCP).
Second, more effort is needed to detect foreign interference, including offline and non-state efforts. Because democracies have a natural aversion to government surveillance, a better answer than simply stepped-up government monitoring may be supporting non-profit, non-government initiatives and independent media.
Third, effort is needed to develop better ways to measure the impact of foreign interference to allow for a more informed decision on resourcing efforts to counter it. Notwithstanding the lack of current empirical data on impact, opinion polling points to a perception that foreign interference will occur and, in places such as the US, a view by many that the 2016 presidential election was swayed by it (a credible view, given the narrowness of the outcome). Research is needed to measure the effectiveness of different education and awareness efforts to address these concerns.
Fourth, public funding may be needed to better secure political parties and politicians from cyber intrusions. Finally, democracies need to impose costs on the two primary state actors: they should consider joint or regional action to make future or continued interference sufficiently costly to those states that they will no longer pursue it. Legislation may also be needed to make it more difficult for foreign adversaries to operate (being mindful of the differing objectives of the two main actors); this may be a second best for countries that find it too difficult to call out adversaries.
Introduction
In 2016, Russia comprehensively and innovatively interfered in the US presidential election, offering a template for how democracies around the world could be manipulated.1 Since then there have been 194 national-level elections in 124 countries and an additional 31 referendums.2 This report seeks to catalogue examples of foreign interference in those polls and group them into three ‘buckets’:
- interference targeting voting infrastructure and voter turnout
- interference in the information environment (to make the scope manageable, we have focused on interference surrounding elections, but it’s apparent that such efforts continue outside election periods as part of longer term efforts to manipulate societies)
- longer term efforts to erode public trust in governments, political leadership and public institutions.
This research focused on cyber-enabled interference (including, for example, information operations that harness social media and breaches of email and data storage systems), but excluded offline methods (for example, the financing of political parties and the suborning of prominent individuals).
The yardstick for counting an activity as interference was that proposed by former Prime Minister Malcolm Turnbull, who put it this way when introducing counter-foreign-interference laws in Australia in 2017: ‘we will not tolerate foreign influence activities that are in any way covert, coercive or corrupt.
That’s the line that separates legitimate influence from unacceptable interference.’3 A major issue has become the public perception that results may have been swayed, with consequences for the direction of these states’ policies and actions, together with a loss of public trust in democratic institutions and processes.
Multi-country Pew Research Center polling shows that there’s an increasing expectation among global publics that elections will suffer interference: majorities (including 65% of Australians) in 23 of 26 countries surveyed in 2018 said it was very or somewhat likely that a cyberattack would result in their elections being tampered with.4
In some cases, such as the 2016 US presidential election, polling shows that a large proportion of people (39% of US adults) feel that Russian meddling swung the election,5 which is probably the most valuable outcome Russia could have hoped for, given that it’s seeking to undermine confidence in US global leadership and the US public’s faith in the nation’s democratic process.6
Since that election, reports of foreign interference in democratic elections have continued to surface. This suggests a belief among adversary states that interference is serving their interests and that the costs of action are not sufficiently high to deter this behaviour.
Of course, foreign governments interfering in elections is nothing new.7 While the objectives might be similar to those of Cold War style efforts, the means are different. Today, a state such a Russia is able to reach more than a hundred million Americans through a single platform such as Facebook without sending a single operative into US territory.8 Or, as nearly happened in Ukraine, the official election results can be remotely altered to show a candidate who received just 1% of the vote as winning.9
And, significantly, a little effort goes a long way: in 2016, Russian operatives were able to organise two opposing groups to engage in a protest in front of the Islamic Da’wah Centre of Houston for ‘the bargain price of $200’.10 Having a big impact is now much easier, cheaper and less risky. For democratic governments, responding can be extremely difficult. The methods used by adversaries typically exploit treasured democratic principles such as free speech, trust and openness. Detection can be hard both because the methods are difficult to identify and because democracies avoid surveillance of their own domestic populations and debates (outside niche areas such as traditional criminal and terrorist activity). Typically, the bulk of intelligence resources is directed towards external collection, and domestic populations are rightly wary of increased government monitoring.
Democratic governments themselves can be obstacles: if the winning party believes it benefited from the foreign interference or would be delegitimised by admitting its scale, it can even mean the newly elected government will play down or ignore the interference. Tensions in the US in the wake of Russian interference in the 2016 election point to the potential for these sorts of issues to arise.11
Measuring levels of interference and adversary’s objectives is another challenge. Given the difficulty of detection and the variance in methods employed, it’s hard to compare relative levels of interference across elections. Objectives are also not always straightforward. Most efforts to interfere in elections are not about directly altering the vote count. Instead, many appear aimed at disrupting societies or undermining trust in important institutions. There also appear to be different overarching aims depending on the adversary involved.
Project overview and methodology
This research was generously supported by the Australian Computer Society and stemmed from a series of engagements with policymakers on countering election interference. Desk research and interviews focused on developing a database of cyber-enabled foreign interference in democratic elections. It was informed by a full-day workshop in London involving several electoral commissioner equivalents from around the world as well as the President of the Australian Computer Society. A key focus of the workshop was the development of a framework for mapping election interference with a view to improving the policy response.
The start date for the research was the 2016 US presidential election and the end date was April 2019. During that period, this research identified 194 national-level elections in 124 countries and an additional 31 referendums.
Using Freedom House’s Freedom in the world report,12 of the 124 states that have held national elections since November 2016, 53 are considered ‘free’, 45 ‘partly free’ and 26 ‘not free’. Given the focus of this report on democracies, we limited the research scope to the 97 countries that held elections and that were deemed free or partly free.
As noted above, examples of foreign interference were grouped into three buckets. This built off and expands on a framework in the International Cyber Policy Centre’s Securing democracy in the Digital Age report.13
Categorising incidents was an inexact science. Often there was a lack of publicly available information about the case (many media reports described ‘hacks’ without elaborating), or it might easily straddle more than one category. Consider the intrusion into Australia’s parliament and three political parties reported by Prime Minister Scott Morrison on 18 February 2019,14 suspected to have been carried out by Chinese state-sponsored actors. The intent behind this incident is still unclear.
Was it solely espionage or an act of foreign interference?15 The sophisticated state actor has not seemed to use any material obtained to interfere in the current election. That may be because of the discovery of the intrusions, or because the information obtained is being used for a different purpose (as suggested by ASPI’s Michael Shoebridge16). For the purposes of this report, it was classified as ‘long-term erosion of public trust’, given that the public reporting highlighted inadequate security
among core Australian institutions.
This report captures examples of interference that were executed (for example, Russian online disinformation campaigns that ran on social media during the 2016 US presidential election) and those that were discovered but not executed (such as Russians’ accessing of US voter rolls during that election without manipulating or using them).
Findings
Of the 97 national elections in free or partly free countries reviewed for this report during the period from 8 November 2016 to 30 April 2019, a fifth (20 countries) showed clear examples of foreign interference, and several countries had multiple examples (see the appendix to this report).17 It’s worth noting that confidence in attributions to foreign actors varied widely. In ideal circumstances, a government source made the attribution, but often the attribution was more informal. Our intention was not to provide an exhaustive list of every alleged case of foreign interference but instead to capture the spread of states experiencing the phenomenon and illustrative examples of different methods. Details on all examples identified through this research are set out in the appendix.
Country analysis
Of the 97 elections and 31 referendums reviewed, foreign interference was identified in 20 countries: Australia, Brazil, Colombia, the Czech Republic, Finland, France, Germany, Indonesia, Israel, Italy, Malta, Montenegro, the Netherlands, North Macedonia, Norway, Singapore, Spain, Taiwan, Ukraine and the US.
Of those 20 states, 14 were deemed ‘free’ and 6 ‘partly free’. Just over half (12 of 20) of the states were in Europe, which is unsurprising given Russia’s leading role in this area (Table 1).
Table 1: Regional spread (alleged actor)

Table 1 shows the strong geographical link between the target and actor. With the exception of one anomalous case involving the UK (which was alleged to have supported a Yes campaign in a Montenegrin referendum), Russia was the only state interfering in European elections. Similarly, in the Indo-Pacific, China was the only actor (except for Indonesia, where Russia was also involved). Iran’s interference in Israel has a clear connection to its adversarial relationship. In the Americas, there’s more diversity among the actors, but Russia remains the dominant player.
China’s versus Russia’s motivations
Russia’s and China’s interference reflect different national approaches. For Russia, a key objective is to erode public trust in democracies and to undermine the idea that democracy is a superior system.18 This might be driven by President Putin’s personal drive to make the West ‘pay’ for its destruction of the Soviet bloc and by the desire to mount a case inside Russia that democracies are flawed and therefore not a model that Russians should aspire to. As a consequence, Russian interference is inherently destructive to democratic systems, even at the same time as Moscow may seek to promote a party or a candidate thought to be more sympathetic to its interests.19
Chinese interference seems more strategically focused on ensuring that its interests are promoted across all party lines. Unlike the Russian stance, one party’s interests don’t appear to be favoured at the expense of others (with the exception, perhaps, of Taiwan20). Instead, all consequential parties are in its crosshairs with a view to making them more sensitive to core CCP interests. China also seems to pursue a broader front of influencing activities (many of which aren’t captured by this report’s focus on cyber-enabled methods), which can include financial donations,21 aligning the policy interests and public comments of party figures to CCP political goals and suborning prominent individuals to advocate for Beijing’s interests. China doesn’t seem to be as openly intent on doing damage to the credibility of foreign political systems so much as aligning those systems to its strategic objectives.22
Methods
A review of the dataset reveals considerable repetition in methods. There are multiple examples of social media platforms being exploited to reach target populations, often used in concert with state-sponsored media outlets. There is, however, considerable variation in the way social media are exploited. This ranges from organising rallies and amplifying the voices of favoured groups to suppressing voter turnout and exacerbating existing divisions.23 There are also several examples of system breaches, again to pursue different ends, including stealing and leaking emails and accessing voter rolls.
Given the lack of detail in many media reports on foreign interference, it’s difficult to provide a list of the most common methods. Frequency of use also does not translate into impact. For example, the breach of one person’s email account (such as the account of Hillary Clinton’s campaign chair, John Podesta) can have much greater impact than any single social media post or perhaps all of them.
Types of interference
This section examines our three defined buckets of interference.
Targeting of voting infrastructure and voter turnout
Direct tampering with election results is perhaps the most affronting form of foreign interference because it most directly overturns the will of the people.
Ukraine has long been one of the main targets of Russian election interference efforts and has also suffered the most egregious effort to alter the technical results of an election. As Mark Clayton reported back in 2014 (a date outside the scope of the mapping period covered by this report):
Only 40 minutes before election results were to go live on television at 8 p.m., Sunday, May 25, a team of government cyber experts removed a ‘virus’ covertly installed on Central Election Commission computers, Ukrainian security officials said later.
If it had not been discovered and removed, the malicious software would have portrayed ultra-nationalist Right Sector party leader Dmytro Yarosh as the winner with 37 percent of the vote (instead of the 1 percent he actually received) and Petro Poroshenko (the actually [sic] winner with a majority of the vote) with just 29 percent, Ukraine officials told reporters the next morning.24
There are multiple means by which adversary states could interfere with the technical results of elections. Various methods could be used to prevent citizens from being able to vote (for example, by rendering electronic voting booths unusable or corrupting the voter roll so eligible voters are removed and turned away from voting booths25) or reducing the turnout of certain voter groups with known dominant voting behaviours (for example, via online campaigns that encourage a boycott26 or targeted misinformation that has the effect of deterring certain voter groups27).
The result itself could be altered via various means. Electronic voting booths could be maliciously programmed to record a vote for Candidate A as a vote for Candidate B instead, the transmission of votes tallied at individual voting booths could be intercepted and altered, affecting the final tally, votes in the central tally room or system could be altered remotely or, as was attempted in Ukraine, the release of the vote outcome could be tampered with (a tactic unlikely to go unnoticed, but likely to cast doubt among some about the integrity of the poll and of the national electoral system).
Research for this report identified six countries that had experienced interference targeted at voting infrastructure and voter turnout: Colombia, Finland, Indonesia, North Macedonia, Ukraine and the US (Table 2).
Table 2: Targeting of voting infrastructure and voter turnout
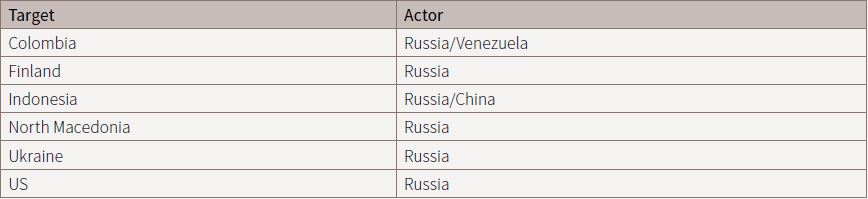
Examples included the targeting of voter registration rolls in Colombia,28 Indonesia29 and 21 US states,30 a denial of service (DoS) attack on a Finnish web service used to publish vote tallies,31 a distributed denial of service (DDoS) attack on Ukraine’s Central Election Commission,32 and the use of social media to suppress voter turnout in North Macedonia33 and in the US.34 In the US, an Oxford University report noted that Russian operatives tried to suppress the vote of African-Americans by pushing the narrative that ‘the best way to advance the cause of the African American community was to boycott the election and focus on other issues instead’.35 While it’s difficult to determine the effect of the disinformation campaign by Russia’s Internet Research Agency, the Pew Research Centre reported that the voter turnout of African-Americans fell in 2016 (see appendix, page 19).36
The attackers identified in public reports (sometimes speculatively) were Russia (in one instance, combined with Venezuela) and China. Russia was by far the dominant actor.
Interference in the information environment around elections
It’s difficult to detect foreign interference during elections with high confidence in a timely manner.
Consider this example from Bret Schafer, which fooled multiple media outlets: Have you met Luisa Haynes? She was a prolific force in the #BlackLivesMatter community on Twitter. In just over a year, she amassed more than 50,000 followers; and her outspoken, viral takes on everything from Beyoncé to police brutality earned her hundreds of thousands of retweets and media coverage in more than two dozen prominent news outlets.
She was, on the surface, a symbol of a new generation of Black activists: young, female, and digitally savvy—except—she was fake.37
At the International Cyber Policy Centre, journalists periodically approach us about websites and social media accounts they suspect are run by foreign agents or trolls. Mostly, investigations lead to dead ends, or to apparently real people who are hard to definitively classify as foreign trolls rather than colourful citizens.
Now that the traditional media have lost their old gatekeeper role and control over the information environment, it’s far easier for foreign adversaries to inject themselves into national debates and much harder to trust what you’re reading and seeing. When Australians were asked in 2018 ‘Do you feel like the news you read or watch gives you balanced and neutral information?’, 54% said ‘never’ or ‘rarely’. There were similar results in democracies around the world38 (in historical terms, in the US the proportion of people reporting ‘a great deal’ and ‘quite a lot’ of confidence in newspapers has dropped from a high of 39% in 1990 to 23% in 201839).
While avenues for altering the technical results of elections are limited, opportunities to manipulate the information environment are limited only by creativity. Methods might include amplifying a party’s existing narrative using social media accounts that have assiduously built up followers over lengthy periods,40 or creating and spreading disinformation to undermine a candidate (for example, the state-owned Russian news agency Sputnik calling French presidential candidate Emmanuel Macron an agent of ‘the big American banking system’).41 It might involve infiltrating genuine activist groups and attempting to increase polarisation,42 or it could involve the creation of fake personas who provide inflammatory commentary on divisive issues, as with Luisa Haynes. Often such campaigns seek to prey on and exacerbate existing social cleavages with a view to exploiting them to manipulate the information environment in the desired direction.
While the impact of this manipulation isn’t as direct as interfering with key election infrastructure, its ease and cheapness, combined with the difficulty of timely detection, make it a preferred method. Foreign interference in the information environment was identified in 10 states: France, Israel, Italy, Malta, the Netherlands, North Macedonia, Spain, Taiwan, Ukraine and the US (Table 3).
Table 3: Interference in the information environment

Examples included information disruption campaigns targeting French presidential candidate Emmanuel Macron (such as the theft and release of 21,000 emails just before the final vote in the election—a technique likely to be of enduring utility for adversaries)43 and the spreading of disinformation by Russian media outlets Russia Today (RT) and Sputnik in Catalonia44 and Italy with headlines like ‘Migrant chaos, the beginning of a social war’45 or claiming in the Macedonian referendum that, depending on who won, Google would remove Macedonian from its list of recognised languages.46 Chinese-backed disinformation campaigns targeting Taiwan were reported as using zombie accounts and China’s so-called ‘50 Cent Army’ of online trolls and commentators to amplify the dissemination of disinformation.47 In Ukraine, Russia sought to buy or rent Ukrainian Facebook accounts to disseminate disinformation.48 There was also an unusual case of the UK’s Foreign and Commonwealth Office being accused of funding British PR agency Stratagem International to help the Macedonian Government with its ‘Yes’ campaign on the changing of the country’s name, thereby opening up the opportunity for Macedonia to join the EU and NATO.49
Research identified four alleged actors: Russia (the most dominant by far), China, Iran and the UK.
Long-term erosion of public trust in public institutions
Perhaps the most pernicious aspect of foreign interference is the longer term corrosion of public trust in the institutions that underpin democracy.
For example, the Center for Strategic and International Studies’ Defending Democratic Institutions Project has looked at Russian efforts to weaken trust in the rule of law as administered by the justice systems in both the US and Europe.50 In Australia, China is alleged to have attacked the Australian Parliament in 2011 and 2019, as well as three political parties in 2019.51 And in several countries attacks on electoral commissions responsible for impartially conducting elections have been reported.52
If foreign adversaries can destroy trust in these pillar institutions and related organs of democracy, democracy quickly unwinds.
Making this phenomenon even harder to confront, it’s often not immediately clear whether a campaign is being run by a nation-state or by conspiracy-oriented individuals. During the Brexit vote in the UK, what appeared to be a conspiracy theory (that had first surfaced during the 2014 Scottish referendum) spread online, urging voters to use pens, not pencils, to complete their ballot papers.53
The not-so-subtle inference was that government officials were rubbing out ballots completed in pencil and changing people’s votes (figures 1 and 2).
Figure 1: ‘I voted in pencil’

Source: Professor Brian Cox, Twitter, 23 June 2016.
Figure 2: ‘Use pens plea’

Source: BBC News, 22 June 2016.
It’s difficult to know how damaging these sorts of campaigns are for public trust in critical democratic institutions or whether they’re state-backed. What’s apparent is that polling has picked up distrust in key electoral institutions. The Australian voter experience report revealed that just 42% of Australians have a great deal of confidence in the Australian Electoral Commission’s ability to conduct an election, while a further 43% have ‘some’ confidence.54 In the UK, just 21% reported that they were ‘very confident’ and 48% said they were ‘fairly confident’ that the 2015 election was well run.55 While electoral commissions are generally off voters’ radars, trust in democracy collapses if people lose trust in those organisations’ ability to conduct elections impartially.
More significantly, there’s also been a dramatic drop in levels of satisfaction with democracy in Australia. Although once again it’s hard to track a causal relationship, it seems likely that democracies experiencing rising dissatisfaction with democracy would be more vulnerable to interference. The Australian voter experience report noted that just 55% of Australians “are satisfied with the way democracy works in their country nowadays. This places Australia on the lower end of established democracies, which typically have rates of satisfaction that exceed two-thirds. Historical data indicates that there’s been a dramatic fall in satisfaction. Data from the Australian Election Study in 2007 indicated that 86% reported being satisfied with democracy, falling to 72% in 2013”.56 Surveys such as the Lowy Institute Poll have tracked this dissatisfaction with democracy and speculated about its causes, but with no definitive answers.57
The Democracy Perceptions Index 2018 provides hints to the growing levels of public distrust in democracies around the world. It found that 64% of the public in ‘free’ countries (as defined by Freedom House) said their government ‘never’ or ‘rarely’ acts in their interest, compared to 41% in ‘not free’ countries. In Australia, a third of Australian adults say the government ‘mostly’, ‘often’ or ‘sometimes’ acts in their interest (67% say it does so ‘never’ or ‘rarely’).58 While this is a large proportion of the population, it hasn’t yet resulted in French-style yellow vest protestors.59
In Australia and elsewhere, it’s highly unlikely that this dissatisfaction is driven entirely by foreign interference. Anxiety about large economic and social changes brought about by globalisation and technological development could all be in play.60 Longitudinal Gallup surveys have also picked up a long downwards trend in average trust in public institutions (Figure 3).61
Figure 3: Americans’ average confidence in public institutions over time

Quantifying examples of the long-term erosion of public trust is perhaps the trickiest of tasks, as in many cases more immediate efforts to shape public opinion (such as spreading disinformation) also have the longer term impact of eroding public trust in the media and other institutions. Efforts to erode public trust also typically exploit existing societal cleavages,62 making detection difficult and any additional impact from interference on pre-existing divisions hard to measure. However, for the purposes of this research, 10 states were identified as having experienced efforts to create long-term erosion of public trust: Australia, Brazil, the Czech Republic, Germany, Montenegro, Norway, the Netherlands, Singapore, Ukraine and the US (Table 4).
Table 4: Long-term erosion of public trust

Examples have included the use of social media bots in Brazil to question the democratic model,63 amplification by Russia using Twitter bots of far-right Alternative für Deutschland’s warnings about election fraud,64 and systematic efforts by Russia to weaken ‘faith in the rule of law as administrated by the justice system’ in the US through the use of disinformation and the exploitation of ‘legitimate criticisms of the justice system’.65
The two identified actors in this category were Russia and China.
Limitations
There are several notable limitations to this research.
First, we focused on states and therefore missed private actors that are distorting democratic debates in similar ways. For example, there have been several cases of the commercialisation of Russian-like disinformation campaigns. Consider the group in the Balkans that built up popular Facebook pages with titles such as ‘Australians against Sharia’ and ‘Aussie infidels’ that targeted Australians to generate ad revenue.66 Future research could usefully explore the impact that these groups are having and how to counter them.
Second, our focus was on public cases, which perhaps tends to favour the identification of Russian efforts, given Moscow’s more overt and detectable methods and the media’s growing familiarity with its approach. Parallel research on CCP methods that the International Cyber Policy Centre is preparing suggests that Beijing often uses techniques that are harder to detect and longer term and so may be underreported. A broader methodology is probably needed to capture difficult-to-spot influence activities such as subverting policy positions and decision-making as well as long-term campaigns to cultivate supportive political figures and voices and silence, pressure or sideline critics.67
Third, the focus on foreign state actors has, of course, excluded domestic efforts to harness these same techniques, for example by political parties and local activists that may also be contributing to voter dissatisfaction with democracy and trust in institutions.
Fourth, there has been a tendency to favour English-language sources.
Finally, the increasing ability to micro-target voters and the difficulty of detecting many of the types of interference reported here mean that many examples could be being missed in the online information arena. Consider the case of a Russian-operated fake Black Lives Matter Facebook page that was only reported as suspicious because it used the phrase ‘Don’t shoot’—an expression that genuine activists had stopped using.68 The shift by major platforms such as Facebook to move from public broadcasting to private messaging will only accentuate this challenge.69
Findings and recommendations
The motivation behind this research is that, by better understanding the methods being used and the targets of high-activity adversary states, democracies will be able to better assess their existing response and mitigation capabilities and adjust as necessary.
We make the following recommendations.
1. Targets are limited: respond accordingly
Despite the enormous amount of media coverage that’s been devoted to state-backed election interference, the phenomenon isn’t universal. From public accounts, there are two primary actors and they focus judiciously on states that matter to them. Democracies should calibrate their policy responses to the likely risk, methods and adversary. The US and European states are clear targets of the Russian Government; Indo-Pacific nations are targets of the CCP.
2. Build up detection capabilities
More effort is needed to detect foreign interference, including offline and non-state efforts (such as by for-profit groups that misuse social media platforms to stir up hate). Because democracies have a natural aversion to government surveillance, a better answer than simply stepped-up government monitoring may be supporting non-profit, non-government initiatives and independent media. These groups can more credibly monitor for interference and more easily engage at the community level. In smaller states, where local media outlets are disappearing, government subsidies may be needed to ensure sufficient scrutiny of local and state political groups (which are often feeder groups for national politics).
3. Fund research to measure impact and measure the effectiveness of education campaigns to address public concerns
Governments should fund research to develop better ways to measure the impact of foreign interference to allow for a more informed decision on resourcing efforts to counter it. Notwithstanding the lack of current empirical data on impact, opinion polling points to a perception that foreign interference will occur, and in places such as the US to widely held views that elections have been swayed. Various efforts have been made to respond, including fact-checking services,70 opening up social media data streams to election-oriented academic research,71 and legislation to counter fake news.72 Research is needed to understand which efforts are most effective, after which those tougher measures should be twinned with public awareness campaigns to address these concerns.
4. Publicly fund the defence of political parties
Political parties and politicians are clear targets of foreign adversaries. With their shoestring budgets and the requirement to scale up dramatically during election campaigns, they’re no match for the resources of sophisticated state actors. Politicians are also vulnerable, including through the use of their personal devices. There’s a strong public interest in preventing foreign states from being able to exploit breaches of both parties and individual politicians to undermine domestic political processes. Democratic governments should consider public funding to better protect all major political parties and to step up cybersecurity support to politicians.
5. Impose costs
Democracies need to look at better ways of imposing costs on adversaries. Because of spikes in interference activity around elections, they can be prone to being picked off or to discounting interference if the party that won benefited from it. Democracies should consider concerted joint global or regional action that looks beyond their own particular cases as well as more traditional approaches such as retaliatory sanctions. Legislation may also be needed to make it more difficult for foreign adversaries to operate (being mindful of the differing objectives of the two main actors)—this may be a second best for countries that find it too difficult to call out adversaries.
6. Look beyond the digital
Russian interference is detectable, if not immediately, then often after the event. This has generated a natural focus on Moscow’s methods and activities. However, there are many more subtle ways to interfere in democracies. Research like this that focuses on digital attack mechanisms also misses more traditional and potentially more corrosive tactics, such as the provision of funding to political parties by foreign states and their proxies and the long-term cultivation of political influence by foreign state actors. Australia has recently passed legislation to counter more subtle forms of foreign interference73 that were starting to be detected.74 States, particularly those in the Indo-Pacific, should be attuned to these types of interference and make preparations to prevent, counter and expose them.
7. Look beyond states
Troubling public perceptions of democracy are unlikely to be explained by foreign interference alone. Foreign interference may, however, magnify or exploit underlying sources of tension and grievance in particular societies. A thorough response by government and civil society needs to consider a wider set of issues and threat actors, including trolls working for profit, and the health of the political and media environment (including by ensuring that local and regional media remain viable or are adequately funded).
Appendix
Examples of foreign interference (November 2016 to April 2019)
Sources for all examples can be found in Table 5 of the accompanying report.
ASPI International Cyber Policy Centre
The ASPI International Cyber Policy Centre’s mission is to shape debate, policy and understanding on cyber issues, informed by original research and close consultation with government, business and civil society.
It seeks to improve debate, policy and understanding on cyber issues by:
- conducting applied, original empirical research
- linking government, business and civil society
- leading debates and influencing policy in Australia and the Asia–Pacific.
The work of ICPC would be impossible without the financial support of our partners and sponsors across government, industry and civil society. This research was made possible thanks to the generous support of the Australian Computer Society (ACS).
Important disclaimer
This publication is designed to provide accurate and authoritative information in relation to the subject matter covered. It is provided with the understanding that the publisher is not engaged in rendering any form of professional or other advice or services. No person should rely on the contents of this publication without first obtaining advice from a qualified professional.
© The Australian Strategic Policy Institute Limited 2019
This publication is subject to copyright. Except as permitted under the Copyright Act 1968, no part of it may in any form or by any means (electronic, mechanical, microcopying, photocopying, recording or otherwise) be reproduced, stored in a retrieval system or transmitted without prior written permission. Enquiries should be addressed to the publishers. Notwithstanding the above, educational institutions (including schools, independent colleges, universities and TAFEs) are granted permission to make copies of copyrighted works strictly for educational purposes without explicit permission from ASPI and free of charge.
- This has been comprehensively documented; see, for example, Office of the Director of National Intelligence (ODNI), Background to ‘Assessing Russian activities and intentions in recent US elections’: the analytic process and cyber incident attribution, US Government, 6 January 2017, online; PN Howard, B Ganesh, D Liotsiou, J Kelly, The IRA, social media and political polarization in the United States, 2012–2018, Computational Propaganda Research Project, Oxford University, 2018, online. ↩︎
- ElectionGuide: democracy assistance and elections news, online. ↩︎
- Malcolm Turnbull, ‘Speech introducing the National Security Legislation Amendment (Espionage and Foreign Interference) Bill 2017’, 7 December 2017, online. ↩︎
- Jacob Poushter, Janell Fetterolf, International publics brace for cyberattacks on elections, infrastructure, national security, Pew Research Center, 9 January 2019, online. ↩︎
- ‘Americans’ views on Russia, the 2016 election, and US–Russian relations (trends)’, news release, Gallup, August 2018, online. ↩︎
- Matthew Cole, Richard Esposito, Sam Biddle, Ryan Grim, ‘Top-secret NSA report details Russian hacking effort days before 2016 election’, The Intercept, 6 June 2017, online; Zeynep Tufekci, ‘The election has already been hacked’, New York Times, 3 November 2018, online. ↩︎
- Ishaan Tharoor, ‘The long history of the US interfering with elections elsewhere’, Washington Post, 13 October 2016, online. ↩︎
- ‘As many as 146 million people on Facebook may have received information from Russian agency, Zuckerberg says’, PBS News Hour, 9 April 2018, online. ↩︎
- Mark Clayton, ‘Ukraine election narrowly avoided “wanton destruction” from hackers’, Christian Science Monitor, 17 June 2014, online. ↩︎
- Claire Allbright, ‘A Russian Facebook page organized a protest in Texas. A different Russian page launched the counterprotest’, Texas Tribune, 1 November 2017, online. ↩︎
- Karen Yourish, Troy Griggs, ‘8 US intelligence groups blame Russia for meddling, but Trump keeps clouding the picture’, New York Times, 2 August 2018, online. ↩︎












